Ahead of the 2020 US presidential elections next week, Donald Trump's Twitter account remains central to his campaign.
Throughout his presidency, Trump has shared his thoughts, policy and even publicly fired members of his administration, with 87.3 million followers.
With this in mind, it raised a lot of eyebrows when Dutch security expert Victor Gevers claimed to have gained access to the US president's account.
His alleged password was less than secure, 'maga2020!', a play on his 2016 election slogan; 'Make America Great Again'.
Mr Gevers told BreakingNews.ie that it was "manual guesswork" and that it took him just 90 minutes to gain access to Trump's Twitter account.
He guessed right on his fifth attempt.
Lucky guess
"You can try passwords directly after each other. Plus I was busy with something else at the time," he said. "I did not foresee it working. It was literally a lucky guess in a very unpredictable situation."
Mr Gevers is chair of the Dutch Institute for Vulnerability Disclosure, as an 'ethical hacker' his aim is to highlight security issues on social media, particularly two-factor authentication.
I had a hunch that he or his campaign staff might use a password like this.
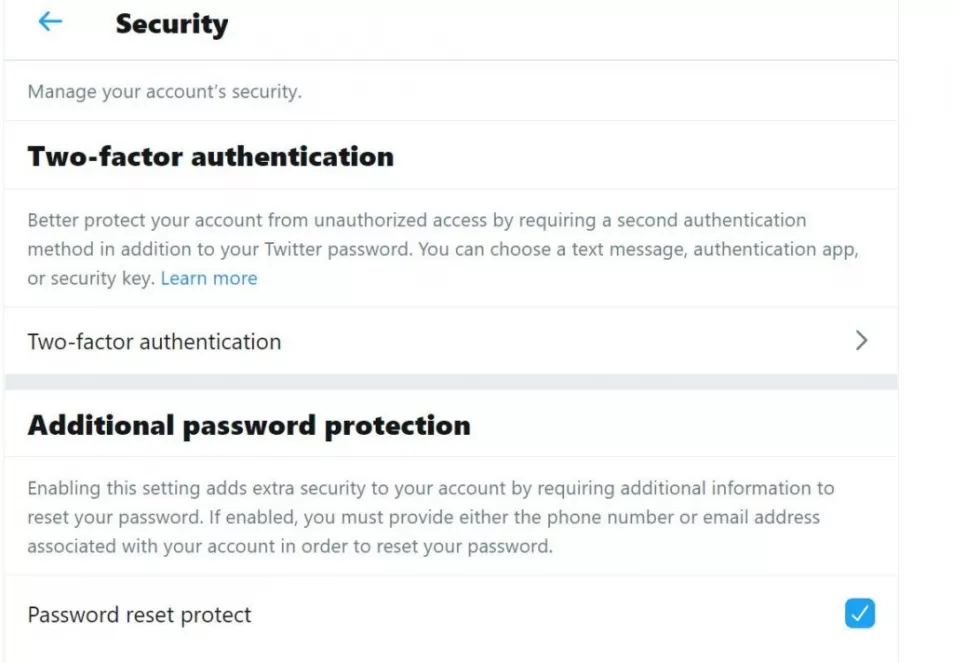
Two-factor authentication is an extra layer of security designed to ensure that you're the only person who can access your account, even if someone knows your password.
Mr Gevers and two other ethical hackers previously gained access to Trump's Twitter account in 2016 and he was shocked to discover two-factor authentication wasn't applied to Trump's account on this occasion.
"I was very surprised because it was enabled in September. We double-checked that before we went on Dutch national television to talk about the case of 2016 to make sure. I checked all US government accounts, and the only one that did not have it enabled was his account. That was the moment I knew I had to try a couple of times. I had a hunch that he or his campaign staff might use a password like this."
After Mr Gevers revealed the hack, the White House and Twitter issued denials.
“We’ve seen no evidence to corroborate this claim, including from the article published in the Netherlands today,” a Twitter spokesperson said. “We proactively implemented account security measures for a designated group of high-profile, election-related Twitter accounts in the United States, including federal branches of government.”
He said it was "remarkable" that Twitter said they found no evidence.
Responsible disclosure
Mr Gevers and his colleagues alert people to their hacks with "responsible disclosures", these disclosures explain security issues so they can be avoided in future.
He explained the decision to go public with the Trump hack was taken when he received no response from US authorities.
"If only one of the many addressed parties would respond with, 'ok, we took care of it,' that would have been enough, and nobody would ever have heard about this case. Especially during election time when tensions are high, just like in 2016.
"The most important thing is that we noticed that shortly after the reporting and countless times of trying to contact them, two-factor authentication was enabled on the account again. I find it remarkable Twitter says that they found no evidence."
Advice is seldom welcome, and those who want it the most always like it the least. But these are some excellent instructions on how to secure your Twitter account in less than five minutes, and it will cost you nothing. https://t.co/kg0S33ifpr
— Victor Gevers (@0xDUDE) October 27, 2020
In the responsible disclosure email sent to Trump, seen by BreakingNews.ie, Mr Gevers included a screenshot of Trump's account showing that he could post tweets in the president's name and change his profile.
The email read: "Dear Mr. Trump,
"I want to inform you that your Twitter account @realDonaldTrump at risk because of the use of a weak password: maga2020!
"Also, two-factor authentication appears to be switched off again. Please also see the email from 28 Oct 2016 with the subject: 'Responsible Disclosure 5131: Infomation disclosure and access to your verified Twitter account.'"
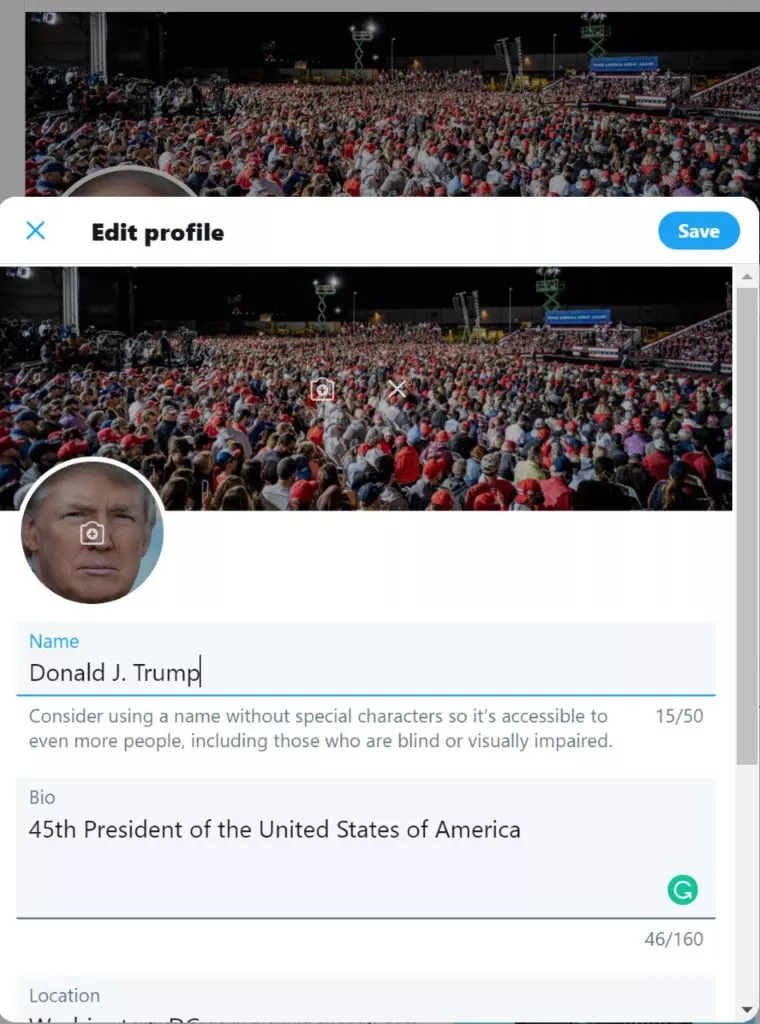
Mr Gevers even suggested a safer password for Trump - '!IWillMakeAmericaGreatAgain2020!'
The disclosure email continued: "In case you need additional information, please do not hesitate to ask.
"Could you please send a confirmation and keep us informed when this issue is fixed?
"GDI.Foundation is a non-profit organization that strives to make the internet safer. We have discovered and reported hundreds of thousands of data leaks and security issues worldwide.
Thank you for your time.
Kind regards,
Victor Gevers
GDI.Foundation"
In the wrong hands, access to Trump's account could lead to anything from a viral tweet to an international incident.
So was there a temptation to change anything?
Mr Gevers replied: "It would be unethical to abuse the account for my benefit. Of course, there is temptation to give your account a follow [from Trump] so that I could send him a DM the next time he uses my research in his executive orders (without using my name)."
He was referring to research he did surrounding security issues with WeChat.
After almost a year, @realDonaldTrump signed Executive Order 13943 for addressing the current issues with WeChat. https://t.co/eBB12D6Ubm
— Victor Gevers (@0xDUDE) September 30, 2020
He added: "But this is not how responsible disclosure works. The DIVD has a strict code of conduct. I train young hackers how to do responsible disclosure so I cannot bend the rules for myself."







